Strengthening Cybersecurity by Implementing the NIST Cyber Security Framework
In today’s interconnected world, where technology is deeply integrated into businesses and corporations, the threat of cybersecurity risks looms large. These risks not only jeopardize the data security of organizations but also pose significant obstacles to achieving business requirements. One effective way to combat these risks is by implementing the NIST Cyber Security Framework, a set of best practices developed by the National Institute of Standards and Technology.
Understanding the Framework
The NIST Cyber Security Framework aims to protect data while remaining cost-effective and flexible enough to suit the needs of various organizations. While implementation is often voluntary, it’s highly recommended to adopt the framework to safeguard against potential data breaches.
Contrary to popular belief, NIST compliance and risk management are not limited to the IT department. Every individual with access to an organization’s computer or information systems plays a crucial role in maintaining cybersecurity standards. Hence, it’s essential for all personnel to be aware of their cybersecurity responsibilities and actively contribute to maintaining a secure environment.
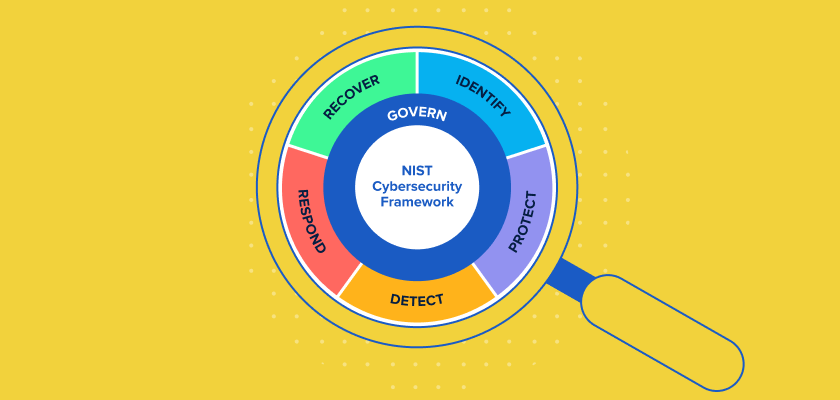
The Core Functions of NIST Cyber Security Framework
- Identify:
- Evaluate and identify cybersecurity risks associated with the business and IT systems.
- Activities include Asset Management, Risk Assessment, and Supply Chain Risk Management.
- Protect:
- Evaluate and protect the business and IT systems from cybersecurity risks.
- Activities include Identity Management and Access Control, Information Protection Processes and Procedures, and Protective Technology.
- Detect:
- Implement methods to detect and reduce the occurrence of cybersecurity incidents.
- Activities include Anomalies and Events, Security Continuous Monitoring, and Detection Processes.
- Respond:
- Develop response processes and procedures to mitigate the effects of cybersecurity incidents.
- Activities include Response Planning, Communications, Analysis, Mitigation, and Improvements.
- Recover:
- Focus on recovering data from compromised files or systems.
- Activities include Recovery Planning, Improvements, and Communications.
Steps for Implementation
- Set Objectives:
- Establish and prioritize the scope of your cybersecurity system.
- Communicate objectives to all personnel to ensure alignment.
- Create a Detailed Profile:
- Tailor the framework to your organization’s specific needs and industry.
- Utilize the NIST Tiers (Partial, Risk-Informed, Repeatable, Adaptive) to categorize your profile.
- Determine Current Position:
- Conduct an independent risk assessment to understand your organization’s current data security position.
- Analyze Gaps and Identify Actions:
- Identify areas of risk and develop strategies to bridge any gaps detected.
- Prioritize areas based on the disparity between Current and Target profiles.
- Implement Plan:
- Develop and implement strategies to remedy areas vulnerable to risk.
- Document processes and develop training materials for personnel.
- Leverage NIST Resources:
- Explore and utilize resources provided by NIST to navigate through implementation processes effectively.
By following these steps and embracing the NIST Cyber Security Framework, organizations can boost their cybersecurity defenses and protect their valuable data assets. Remember, cybersecurity is everyone’s responsibility, and together, we can create a safer digital environment for all. Have a nice day 👋