NIST (CSF)
Leveling Up Your Cybersecurity Game with NIST Framework
Hey, fitness warriors! While you’re busy crushing your workouts and striving for peak performance in the gym, have you ever considered flexing your mental muscles too? Just like maintaining a strong physique is essential for a healthy lifestyle, safeguarding your digital assets is crucial in today’s interconnected world. That’s where the NIST Cybersecurity Framework comes into play – offering a comprehensive guide to managing cybersecurity risks. Let’s break it down and see how you can apply its principles to strengthen your cybersecurity game!
Understanding Cybersecurity Risks
In the fast-paced digital world we live in, cybersecurity risks lurk around every corner, just like plateaus in your fitness journey. From big corporations to individual users like yourself, everyone is susceptible to cyber threats that can compromise your health, safety, privacy, and overall quality of life. It’s essential to address these risks head-on to protect yourself and your digital assets.
The Components of NIST Framework
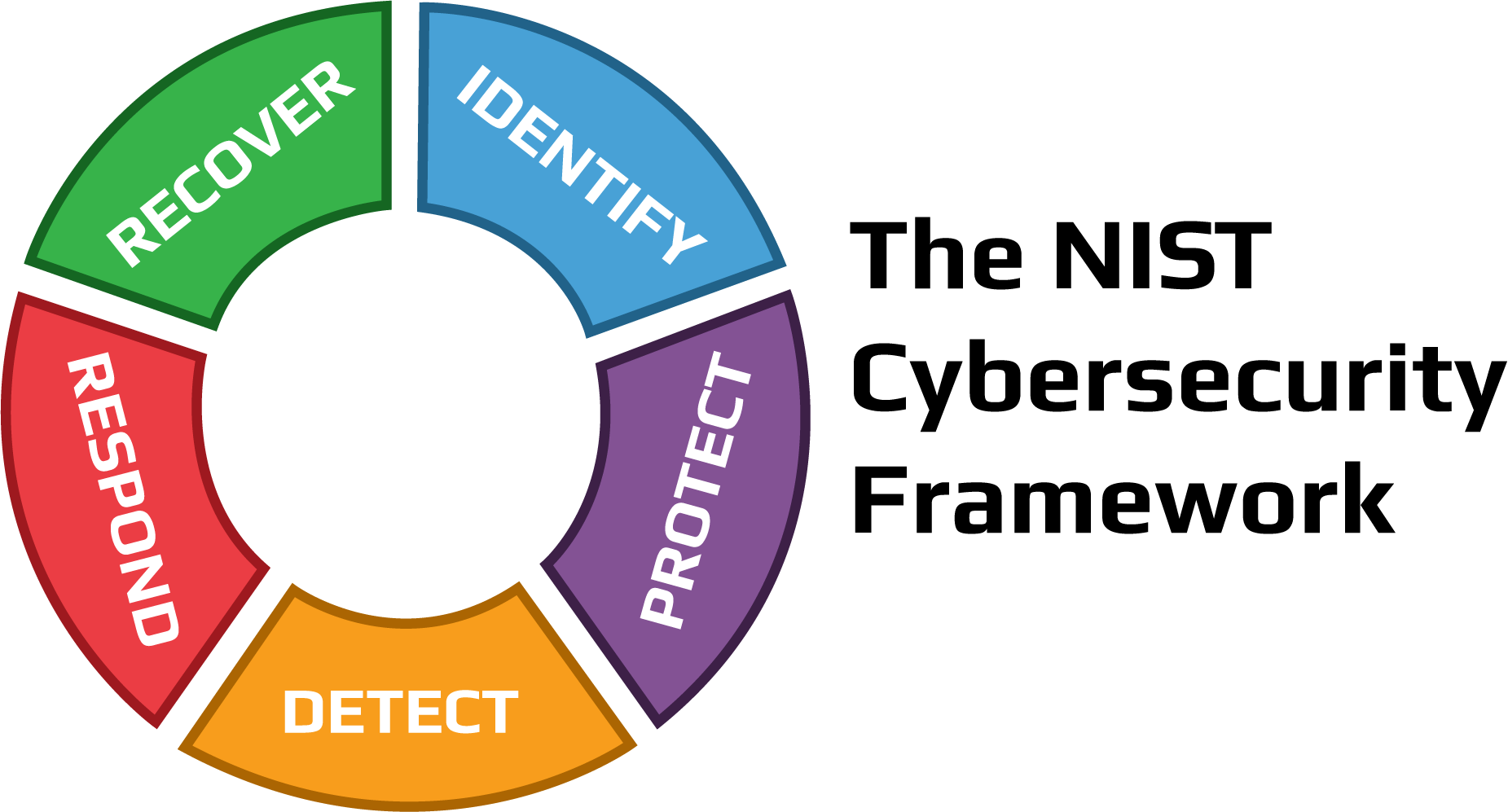
The NIST Framework consists of three main components:
Framework Core:
Think of this as your workout routine – it consists of five core functions: Identify, Protect, Detect, Respond, and Recover. Each function plays a vital role in strengthening your cybersecurity posture, just like different exercises target various muscle groups.Implementation Tiers:
Just as you progress through different levels of difficulty in your workouts, organizations can choose from four implementation tiers based on their cybersecurity practices: Partial, Risk Informed, Repeatable, and Adaptive.Profiles:
Profiles help tailor cybersecurity activities to align with your specific needs and goals, similar to customizing your fitness plan based on your objectives and resources.
Implementation Tiers and NIST Profiles
Implementation Tiers
- Partial (Tier 1): Organizations at this tier have limited cybersecurity capabilities and may lack formalized processes. It’s akin to starting your fitness journey with basic exercises and minimal equipment.
- Risk Informed (Tier 2): At this tier, organizations begin to identify cybersecurity risks and integrate them into their overall risk management processes. It’s like advancing to a more structured workout routine, where you start considering potential risks and adjusting your approach accordingly.
- Repeatable (Tier 3): Organizations at this tier have established cybersecurity processes that are regularly reviewed and improved upon. Similar to progressing to a consistent and effective workout regimen, where you follow a structured plan and continuously refine it for better results.
- Adaptive (Tier 4): The highest tier signifies organizations that have dynamic and responsive cybersecurity practices, capable of adapting to evolving threats. This is like achieving peak fitness, where you’re not only maintaining your progress but also adapting to new challenges and pushing your limits.
NIST Profiles
Every organization has its own unique objectives, requirements, and resources when it comes to cybersecurity. NIST Profiles help organizations compare their current cybersecurity posture (Current Profile) to their desired state (Target Profile). By identifying the gaps between the two profiles, organizations can develop tailored implementation programs to enhance their cybersecurity posture.
Functions of NIST Framework
The functions are divided into 5 parts:
- NIST Framework Core - Identify (ID)
- NIST Framework Core - Protect (PR)
- NIST Framework Core - Detect (DE)
- NIST Framework Core - Respond (RS)
- NIST Framework Core - Recovery (RC)
Let’s relate some key functions of the NIST Framework to your fitness journey:
Protect Function
- Identity Management, Authentication, and Access Control: Just as you secure your gym locker with a strong lock, organizations must control access to their digital assets.
- Awareness and Training: Educating yourself about proper workout techniques is crucial – similarly, employees need cybersecurity training to understand their responsibilities.
- Data Security: Protecting sensitive data is like safeguarding your personal fitness data from unauthorized access.
Detect Function
- Anomalies and Events: Detecting irregularities in your workout routine helps prevent injuries. Similarly, organizations need to identify and assess cybersecurity anomalies to prevent breaches.
- Security Continuous Monitoring: Monitoring your progress at the gym helps you stay on track with your fitness goals. Likewise, continuous monitoring of information systems helps organizations detect cybersecurity events.
Respond Function
- Response Planning: Having a plan in place for emergencies is crucial – whether it’s a cybersecurity incident or a muscle strain at the gym.
- Communications: Clear communication is key during a crisis – whether it’s coordinating with your workout buddy or responding to a cybersecurity incident.
- Analysis: Just as you analyze your workout performance to improve, organizations analyze cybersecurity incident notifications to enhance their response strategies.
Recover Function
- Recovery Planning: Planning for recovery after a cybersecurity incident is like planning your post-workout recovery – essential for getting back on your feet.
- Improvements: Learning from past incidents helps organizations improve their recovery and restoration plans, just like incorporating lessons learned from previous workouts improves your future fitness activities.
- Communications: Keeping stakeholders informed during the recovery process is crucial for restoring trust, much like maintaining open communication with your gym buddies.
Identify Function
- Asset Management: Just like you track your progress and manage your fitness equipment, organizations identify and manage their digital assets based on their importance and risk strategy.
- Business Environment: Understanding the business landscape is crucial for making informed decisions – whether it’s mapping out your workout routine or comprehending the various aspects of your organization’s operations.
- Governance Framework: Effective governance ensures smooth operations – whether it’s governing your own fitness regimen or managing internal and external issues within an organization.
Risk Assessment
- Risk Assessment: Assessing cybersecurity risks is akin to evaluating potential obstacles in your fitness journey. By understanding these risks, organizations can prioritize responses and mitigate threats effectively.
- Risk Management Strategy: Just as you tailor your workout routine to match your fitness goals and constraints, organizations develop risk management strategies to align with their priorities and risk tolerances.
- Supply Chain Risk Management: Considering supply chain risks is essential for maintaining a robust cybersecurity posture – similar to how you consider external factors that may impact your fitness journey.
Protect Function
The Protect function within the NIST Framework Core is dedicated to safeguarding organizational assets and ensuring robust cybersecurity measures are in place. Let’s delve into the key components of this function:
Identity Management Authentication and Access Control (PR.AC)
- This component focuses on controlling authorization, revocation, and auditing processes.
- It ensures that the level of authentication required for users, devices, and assets is aligned with the risk associated with each transaction.
Awareness and Training (PR.AT)
- Users and personnel responsible for security services receive training to understand their cybersecurity responsibilities.
- This component aims to enhance cybersecurity awareness among individuals within the organization, both physically and in cyberspace.
Data Security (PR.DS)
- Preserves and protects data-at-rest.
- Manages the integrity of hardware to prevent unauthorized access or tampering.
Information Protection (PR.IP) Processes and Procedures
- Establishes baseline configurations incorporating security principles.
- Formulates a vulnerability management plan to address potential security weaknesses.
Detect Function
The Detect function of the NIST Framework Core is essential for identifying cybersecurity threats and anomalies. Here’s a closer look at its components:
Anomalies and Events (DE.AE)
- Detects and identifies anomalies and events through various detection activities.
- Assesses the impact and behavior of these anomalies to understand their significance.
Security Continuous Monitoring (DE.CM)
- Identifies cybersecurity events and verifies the effectiveness of protective measures through continuous monitoring of information systems and assets.
- Detects cybersecurity anomalies and events by monitoring network activities and conducting vulnerability scans.
Detection Processes (DE.DP)
- Maintains and tests detection processes and procedures to ensure awareness of anomalous events.
- Defines clear detection roles and responsibilities, with a focus on continuous improvement.
Respond Function
The Respond function is crucial for effectively addressing cybersecurity incidents. Let’s explore its key components:
Response Planning (RS.RP)
- Executes response plans to mitigate the impact of cybersecurity incidents.
Communications (RS.CO)
- Ensures incident responders are aware of their roles and responsibilities during response actions.
- Shares information with external stakeholders to achieve broader cybersecurity situational awareness.
Analysis (RS.AN)
- Investigates notifications sent by detection systems and sets up processes for handling information about vulnerabilities.
Mitigation (RS.MI)
- Contains and mitigates cybersecurity incidents to minimize their impact on the organization.
Improvements (RS.IM)
- Incorporates lessons learned from cybersecurity incidents into response plans.
- Updates response strategies to enhance future incident management efforts.
Recover Function
The Recover function focuses on restoring organizational assets affected by cybersecurity incidents. Here’s what it entails:
Recovery Planning (RC.RP)
- Executes and maintains recovery processes and procedures to ensure the restoration of affected assets.
Improvements (RC.IM)
- Incorporates lessons learned from cybersecurity incidents to improve recovery planning and processes.
- Enhances recovery and restoration plans based on past experiences.
Communications (RC.CO)
- Provides coordination to all relevant parties during restoration activities.
- Manages public relations and communication to repair any reputational damage caused by cybersecurity incidents.
Conclusion
Just as there’s no one-size-fits-all approach to fitness, there’s no universal solution for cybersecurity. The NIST Cybersecurity Framework offers implementation tiers and profiles that allow organizations to customize their cybersecurity strategies according to their specific needs and risk profiles. Whether you’re at the beginning of your cybersecurity journey or striving for peak performance, understanding these tiers and profiles can help you navigate the complex landscape of cybersecurity with confidence and precision. So, just like you tailor your workout routine to achieve your fitness goals, remember to customize your cybersecurity approach to safeguard your digital well-being effectively.
By applying the principles of the NIST Cybersecurity Framework to your digital life, you can build a strong defense against cyber threats, just like you build strength and resilience in the gym. So, the next time you hit the weights or go for a run, remember to flex your mental muscles too – because cybersecurity matters in every aspect of our lives, even in the world of fitness enthusiasts like yourself!
Incorporating the principles of the NIST Cybersecurity Framework into your fitness mindset can help you approach cybersecurity with confidence and resilience. By understanding the importance of asset management, assessing risks, and implementing effective risk management strategies, you can navigate the digital landscape with ease – just like you navigate the gym floor with purpose and determination. Remember, just as consistency and dedication are key to achieving your fitness goals, staying vigilant and proactive in cybersecurity is essential for safeguarding your digital well-being. So, whether you’re hitting the gym or browsing the web, remember to flex your mental muscles and prioritize cybersecurity in every aspect of your life!
The NIST Framework Core’s Protect, Detect, Respond, and Recover functions provide a comprehensive approach to cybersecurity, enabling organizations to effectively manage and mitigate cybersecurity risks. By implementing these functions and their components, organizations can enhance their cybersecurity posture and better protect their assets from potential threats.